|
|
Version
4.1 330 KB EXE |
|
|
A free, standalone command-line utility to run your Windows executable without admin rights or UAC elevationRunWithRestrictedRights.exe is a small Windows command line utility that enables you to launch a Windows application safely & securely, without access to files, printers and other resources available only to administrators. Use RunWithRestrictedRights.exe to start an untrusted application on your desktop or call it from a batch file to run a background task with the full protection of the Windows Integrity Mechanism.
Command-line interface
RunWithRestrictedRights <application> [-w] [-l] [-p] [-v] Where: <application> The full path to the application to be started. Please be sure to enclose the path in quotes if it contains at least one space. Options: -w Instead of returning immediately after launching the application, wait until the application ends. Optional. -l Instead of running the application with Medium Integrity, start it with Low Integrity. Optional. -p Also strip away rights granted from being a member of the "Power Users" group. Optional. -d <sid> Also deny rights to the given SID. -v Produce verbose output. Optional. Upon completion, the exit code is the new process identifier (PID) if the application was successfully started and -1 if it was not. You can access that exit code via the standard ERRORLEVEL variable. Why run an application with restricted rights/permissions?For one reason: Security. As this recent Computerworld article points out, a staggering 94% of Microsoft vulnerabilities can be mitigated by simply turning off Administrator's rights when running applications! The article states:
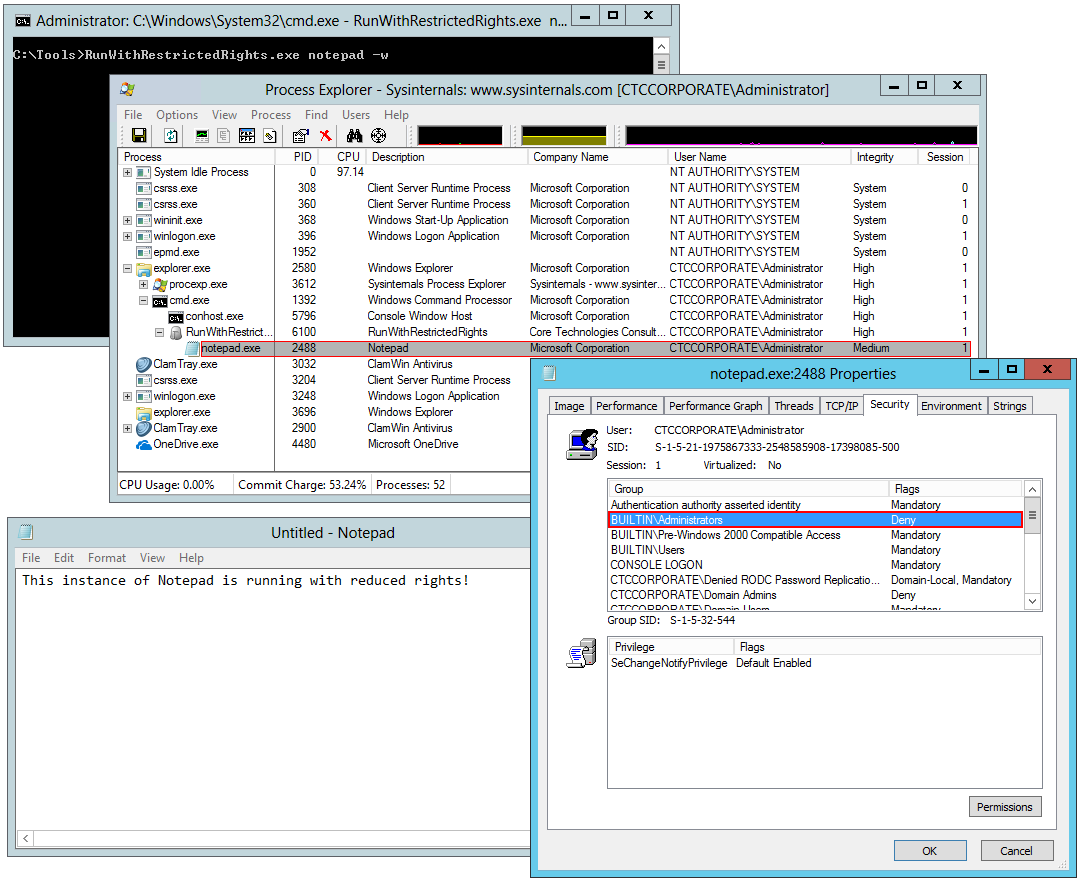
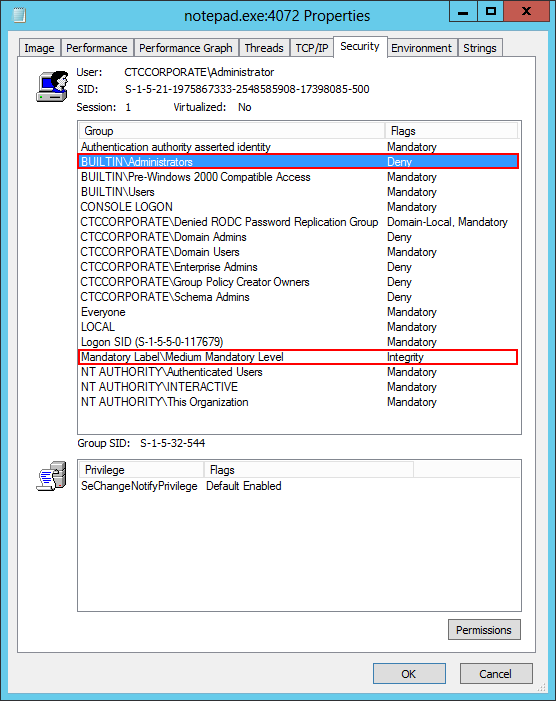
How do I know that my program is running without administrative rights?Confirming that your application is running without admin permisions can be tricky, but Microsoft's free Process Explorer will come to the rescue. Here's a screenshot of Process Explorer interrogating an instance of Notepad launched with restricted rights: A process running with restricted permissions exhibits three telltale signs:
You can find these properties in Process Explorer by double-clicking on your application in the list and switching to the Security tab in the window that comes up. Here we see Notepad running securely: How does this utility compare to Runas?Microsoft's Runas utility can also start a program at one or more levels of authorization. Specifying the "Basic User" trust level (0x20000) is usually enough to run in a "non-elevated" UAC context. However, we encountered a couple of scenarios where Runas wasn't able to cap permissions:
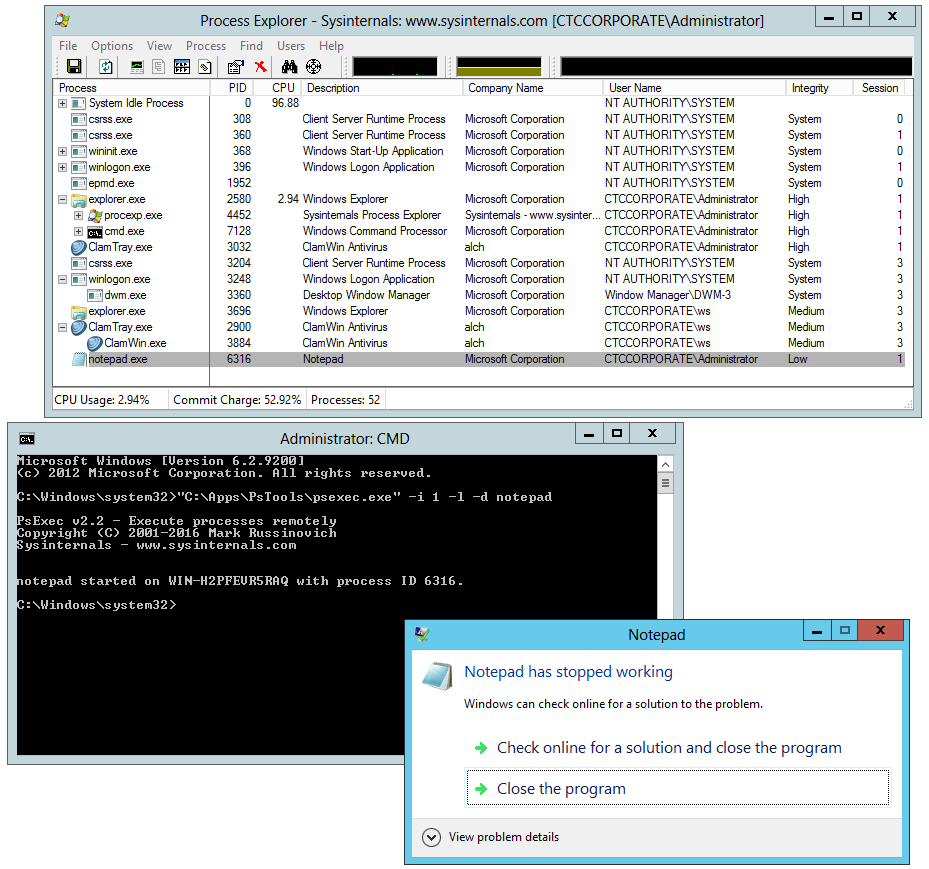
How does this utility compare to PsExec?PsExec.exe, part of Microsoft's versatile PsTools suite, is another free alternative. But we encountered a few barriers using it:
Does RunWithRestrictedRights.exe work on Windows XP and Windows Server 2003, where there is no UAC?Yes, it works well on Windows XP and Windows Server 2003. The Windows Integrity Level can't be set (that feature is only available in Windows Vista and later) but the application is run without admin rights as intended. One note though: If you receive an error stating that "a required privilege is not held by the client", please ensure that your account has these two rights:
|
More InformationDownload |