— Kimberly Z.
Hi, Kimberly.
Even though we’re a tiny company, security is a big deal around here.
Most importantly, we realize that our number one job is to keep customers like you safe, and that our reputation as a trusted, secure software partner depends on doing that.
But it’s not only about protecting our commercial software. Yes, securing our code is very important, but so are the emails we send, the documents we share and the order information we collect. The truth is that all parts of our business must meet a high standard of privacy and security to fulfill our obligations to the hundreds of companies that have put their faith in us.
So let’s dig into the details of our security program to answer your questions. Here are a dozen things that we do to make sure that we are good stewards of your trust.
1. We digitally sign all our products
When you download a program over the internet, how can you be sure that it’s authentic? That it comes to you straight from the authors — and wasn’t doctored to include a virus or malware?
To make sure that you receive our applications tamper-free, we code sign all our executables. That way when you see our company information prominently displayed, you can rest assured that what you’re installing is valid and intact.
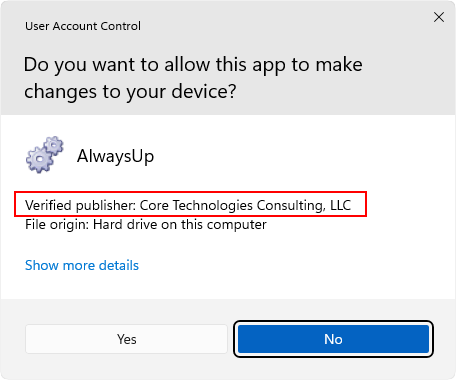
Windows will prompt you with our company information when you’re installing one of our programs:
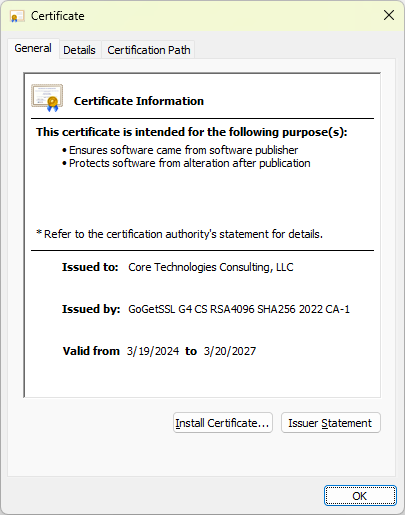
And you’ll always find our digital certificate when you view the properties of any of our secure software:
We should also mention that our company only deploys higher-grade Extended Validation (EV) code signing certificates, which are subject to additional validation and technical requirements. Because of their stringent requirements, only verified, legitimate companies are granted EV certificates.
2. We virus-check every software release
It’s very important to check for viruses at every stage of the software production pipeline. And, most importantly, the final product must be pristine. That’s why we engage third-party services to verify that nothing strange has crept into our software.
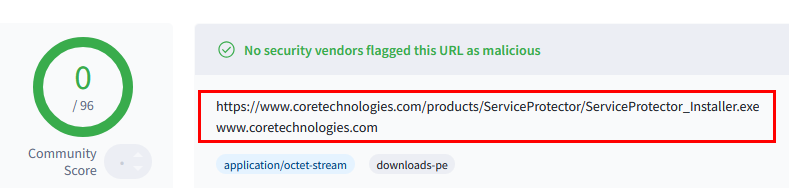
Virustotal — a well-respected online virus-scanning engine owned by Google — is our tool of choice in this area. We run all our applications through Virustotal — and we don’t release if it detects any oddities.
For example, you can see the results of checking Service Protector here. None of the 96 virus scanners found a problem:
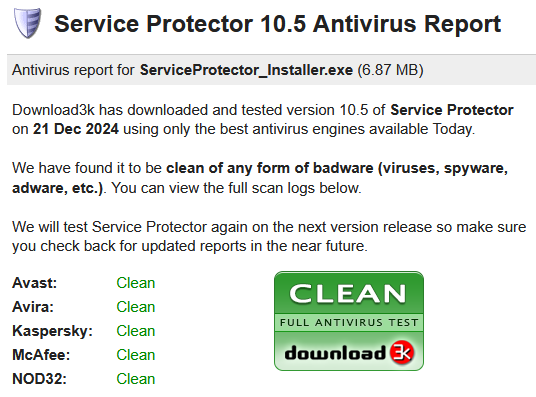
In addition to Virustotal, we also rely on Download3K. They regularly verify our programs with popular antivirus engines, including McAfee, Avast and Avira.
As you can see below, Download3K’s Service Protector Antivirus Report shows no trouble either:
Note that in the unusual circumstance where one of the antivirus scanners actually raises a flag with our software (or site), it usually turns out to be a false alarm. To resolve the issue, we promptly report the details to the antivirus manufacturer and they update their scanners to fix the problem. That happens once or twice a year — often after we publish a new release.
3. We’re trained in secure coding practices

Our team of senior engineers is well versed in secure coding techniques. Indeed, we’ve seen a lot of exploits over the past 20+ years!
But new threats are constantly emerging and resting on our experience is not an option.
To keep us on our toes, regular developer training focuses on the OWASP Top Ten and covers common issues like:
- Buffer overflows
- SQL injection
- Input validation and sanitization
- Cross-Site Scripting (XSS)
Everyone on the technical team must participate.
4. We review 100% of our code for security issues

With our deeper understanding of the pitfalls associated with developing secure software, all code changes must be double-checked for quality, accuracy, and security before committing the updates to our repository. Quite often, that second look identifies edge cases which we must cover prior to release, so it’s well worth the investment.
5. We keep third-party libraries up to date for security

As part of good software hygiene, we regularly update third-party libraries and tools to fix relevant security vulnerabilities. All dependencies are checked at least once per year.
6. We patch our computers regularly

While bulletproofing our code is essential, it’s just as important to secure the supporting systems. That’s why we make it a point to apply operating system patches on a regular basis.
In general:
- Patches to fix critical vulnerabilities are applied as soon as possible — automatically if possible and usually within 30 days.
- On Linux, high, medium and low vulnerabilities are addressed as part of quarterly updates.
- We update Windows machines at least monthly (after Patch Tuesday).
7. We protect all our PC’s with auto-updating antivirus software
All our Windows machines are protected by Microsoft Defender Antivirus, often in conjunction with well-known anti-malware packages like Avira Free Antivirus or Malwarebytes.
Virus definition files are updated automatically and manual scans are performed at least once per year (and whenever anything suspicious happens).
8. Everyone attends annual security training

Each year, our entire staff must attend information security training. The most recent sessions focused on the major threats and defenses relevant to online businesses, including:
- Phishing
- Password hygiene
- Multi Factor Authentication (MFA)
- Ransomware
- Data security and privacy
Side note: If you’re looking for free, high-quality security training modules for your small business be sure to check out Cyber101.com. Their courses are friendly and concise — and the short quizzes after each module do a good job of measuring the learning.
9. We subscribe to industry security alerts

It’s important to be aware of the threat landscape and get an early warning of what other businesses are facing. That’s why we subscribe to several well respected security sources, which keep us in the loop on cyberattacks, ransomware and much more.
Our team relies on timely alerts from:
- Cybersecurity and Infrastructure Security Agency (CISA)
- SecurityWeek
- National Cyber Security Centre (NCSC)
- KnowBe4
10. We’re trained in the ISO 27001 information security framework

In 2025, the chief security principal at Core Technologies Consulting completed Certified ISO 27001 ISMS Lead Implementer Training. The in-depth, 3-day course focused on designing an information security management system (ISMS) and a framework for its continual management and improvement.
The knowledge obtained from the coursework guides our corporate activities — pushing us to maintain confidentiality, integrity and accuracy in everything that we do.
11. We’ve documented (and enforce) our data privacy obligations

Core Technologies Consulting is committed to protecting your privacy. We will never sell, market or abuse your information.
In fact, the limited information we collect when you purchase our software (name and email address) is used only to process your order, notify you of your order status, and assist you after your purchase. Please see our privacy policy for additional details.
12. We’ve created an information security program

Even though we’re a tiny company, we felt that it was important to create an information security program to guide our work.
All employees and independent contractors must read, acknowledge and abide by our ISO 27001-aligned information security policy. We do that because we understand that information security decisions extend well beyond the bounds of the IT department. Everyone is responsible for security.
Hopefully this gives you a better understanding of how we infuse security best practices throughout our company. Thanks again for your question, and, of course, please be sure to get in touch if you have any other questions about our security posture or practices.