 How can I tell if someone updated the services on our Windows 2019 server? Do you have any tools for that?
How can I tell if someone updated the services on our Windows 2019 server? Do you have any tools for that?— Sheldon P.
Hi Sheldon.
Since Windows Services run with high privileges, it’s very important to keep an eye on them. And because of their inherent power, services are a prized target for bad actors looking to hack your system.
Indeed, 2020’s SolarWinds supply chain exploit — one of the worst attacks in the past decade — featured a rogue Windows Service depositing malware in the background. A periodic review of the list of services could have identified the compromise months earlier.
Anyway, our free Windows Service Auditor is an excellent monitoring tool that can help you in your situation. Follow these instructions to keep a watchful eye on your mission-critical servers.
1. Download & run Windows Service Auditor
Windows Service Auditor is portable application, meaning that you don’t need to install it. Simply download the executable file and place it in a folder where you can easily find it.
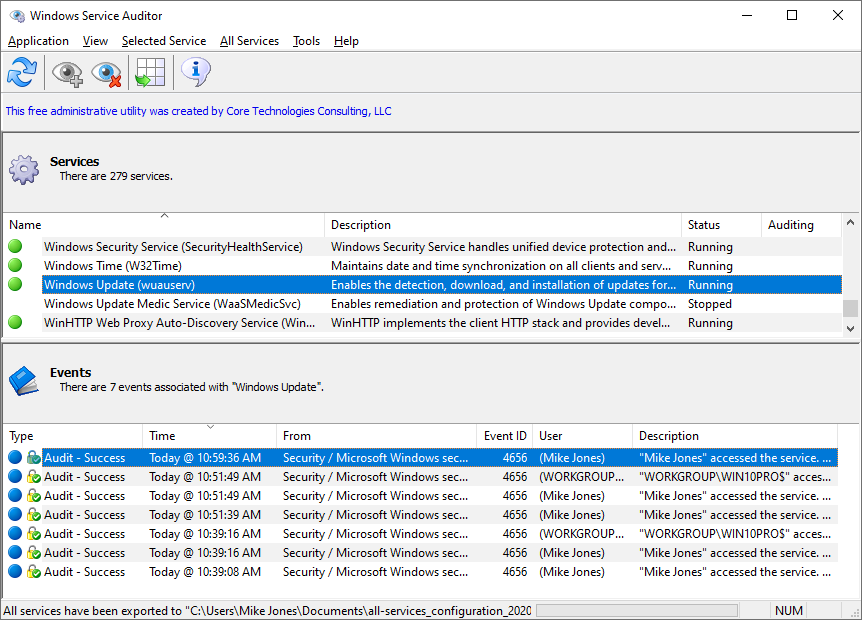
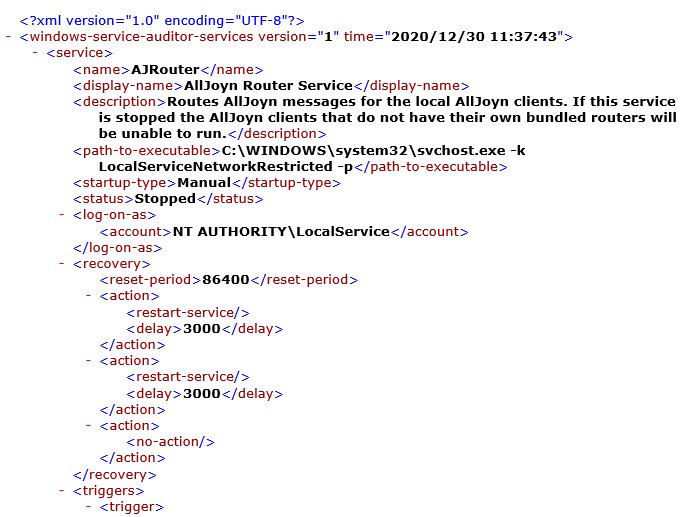
Double-click the file to start it. In a few seconds, a window listing all your Windows Services will appear:
2. Update your computer’s security policy to allow advanced auditing
By default, Windows does not keep track all changes made to Windows Services. That capability must be enabled via advanced security audit policies. Specifically, you need to watch for:
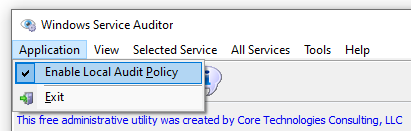
Windows Service Auditor makes it easy to enable that auditing in your local policy. To do so, open the Application menu and ensure that the Enable Local Audit Policy entry is checked:
3. Enable auditing for important Windows Services, to track who starts/stops/changes them
Do you care about the activities of a specific Windows Service? Even though we have enabled advanced auditing in step 2, you must enable auditing for each service that you would like to monitor.
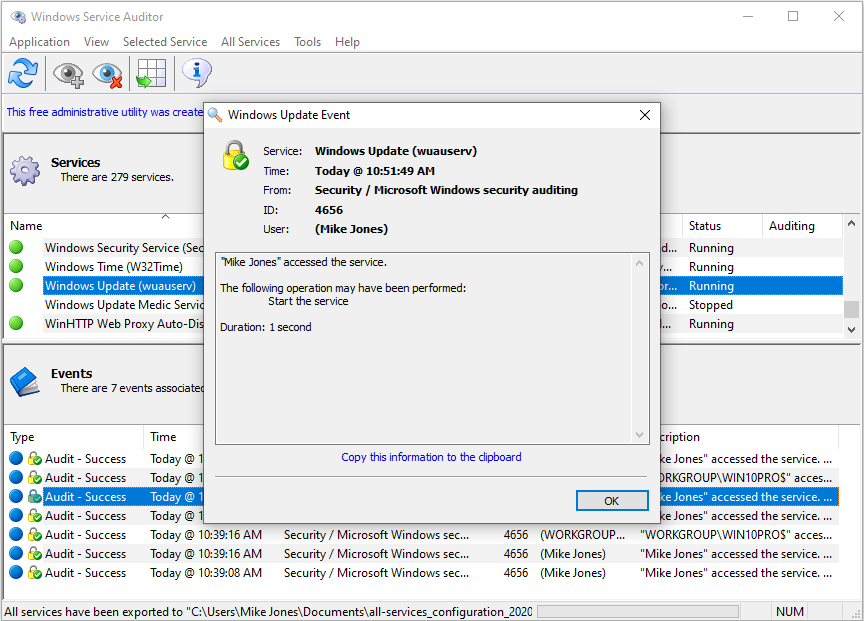
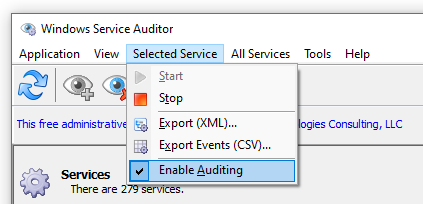
To enable auditing of a service in Windows Service Auditor, highlight the service and check the Selected Service > Enable Auditing menu entry:
With auditing in place for a service, the Windows Event logs will record an event whenever someone attempts to start, stop or modify the service. And to save you from hours of digging through the Event Viewer, Windows Service Auditor will collect those records in the lower Events panel:
4. Capture a baseline snapshot of all services running on your machine
This short video shows how to capture a snapshot of all the services running on your computer:
To summarize:
Start Windows Service Auditor;
Select All Services > Export (XML);
Choose a file name where the services should be saved.
The file will contain an XML record for each service installed on your computer:
5. Compare future snapshots to the baseline, to identify changes
Whenever you want to check if any services have changed, you should:
Create a new snapshot XML file, as described in the previous section;
Using your favorite text comparison tool, compare the new snapshot to the baseline you established in the previous section.
The text comparison tool will highlight all changes that have taken place in between the snapshots.
We recommend using WinMerge — a free, mature text differencing tool for Windows.
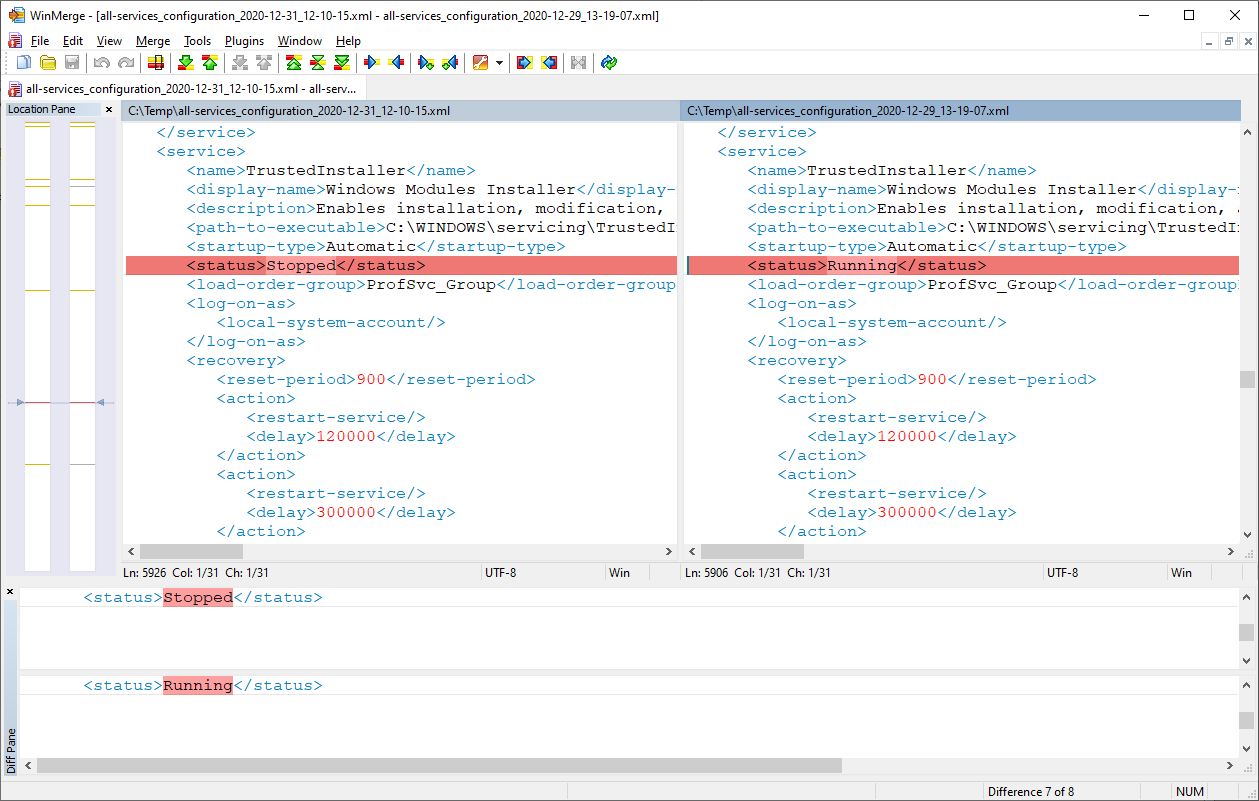
For example, we established a baseline snapshot on December 29. On December 31, we wanted to see what changed with services so we took another snapshot. Afterwards, comparing the two snapshots with WinMerge identified 8 differences, including one showing that the TrustedInstaller service was stopped:
Best of luck managing your system!
UPDATE — September 24 2021: Now find out when a service’s executable has been modified
Windows Service Auditor version 3 includes a few vital improvements that will help you identify when your Windows Services have changed unexpectedly.
And they are just in time, as hackers continue to compromise systems through malware posing as legitimate services!
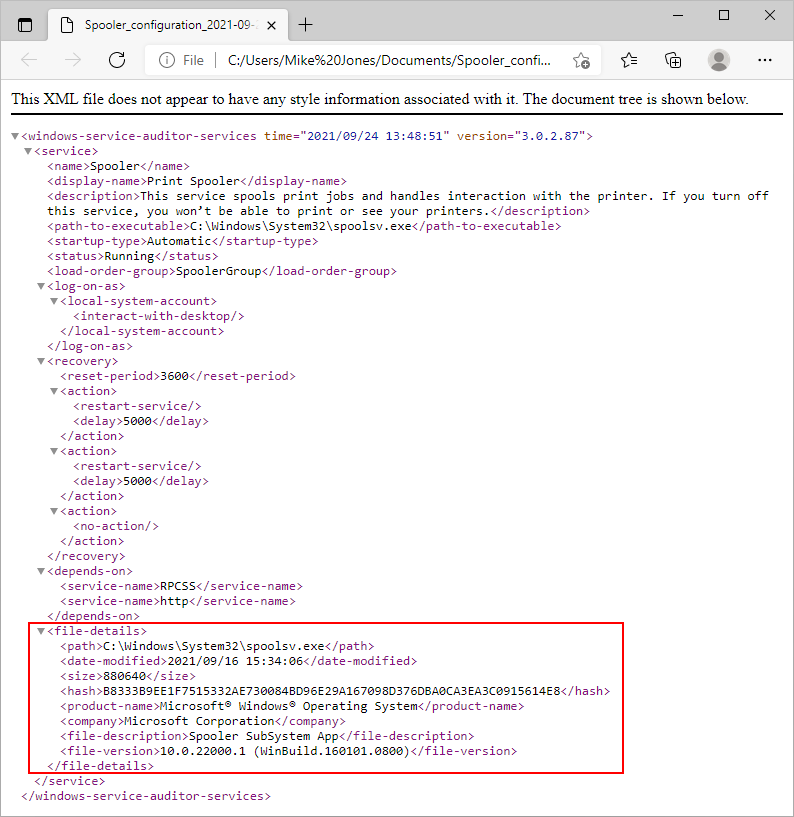
In the new version, Windows Service Auditor now captures the following fields that uniquely identify the executable file supporting the service:
path: The full path to the executable file started by the service.
date-modified: The date and time that the service’s executable file was last modified.
size: The size of the service’s executable file, in bytes.
hash: The SHA-256 hash value of the contents of the service’s executable file. This is a fingerprint that uniquely identifies the executable.
product-name: The “Product name” set in the service’s executable file (visible on the “Details” tab of the file’s properties)
company: The “Company” set in the service’s executable file (visible on the “Details” tab of the file’s properties)
file-description: The “File description” set in the service’s executable file (visible on the “Details” tab of the file’s properties)
file-version: The “File version” set in the service’s executable file (visible on the “Details” tab of the file’s properties)
For example, here is the XML captured for the “Print Spooler” service (which was compromised in June 2021):
With those fields included in the XML, the “diff” outlined above will highlight when the service’s executable has changed. No one will be able to swap out (or impersonate) the underlying file without it showing up on your radar!