Do you have any relevant article that explains how to do this, giving them only the required rights? I don’t want to add them as Power Users or anything like that that might enable them to log in to the server using RDP.
— Gordon
Hi Gordon, thanks for reaching out.
You’re on the right track here. Even though you’ve used Service Security Editor to grant permissions on the service, there’s still one more obstacle to overcome for normal user accounts. Let’s recap and dig into the solutions available.
Service Security Editor enables local control…
As you’ve seen, Service Security Editor will do the heavy lifting. With a few clicks, you can quickly setup your users to start, stop or restart any service you choose. And after your changes, they can use the NET command, the SC command or the Services application — whatever they like.
In our experience, most folks stop here because local control is all they need. But you require remote access as well, and that raises security concerns — especially for accounts without admin rights.
…But Microsoft established additional restrictions on remote access
Starting in Windows 10 version 1709 and Windows Server 2016 version 1709, only users who are local administrators on a remote computer can start or stop services on that computer. This technical article discusses the situation.
To overcome this restriction and allow your users control a service remotely, you have a couple of options. You can either:
Promote your users to administrators on the remote computer. Since the remote access restriction only applies to non-admins, they will no longer be rejected when they come in as an administrator; or
Add your service to the remote access check exemption list — the set of services that bypass the remote access restrictions and can be controlled remotely by normal users.
The first option may be the quickest and most familiar because it’s easy to switch a normal user to an administrator. However, going that route may have unintended security implications. Do you really want to empower your users to do anything they want on the remote server?
The second approach involves editing the registry, which, of course, brings its own concerns. But at least it doesn’t come with hidden security consequences. We recommend going that way, so let’s take you through it in the next section.
How to add your service to the remote access check exemption list
Fortunately, Microsoft makes it fairly easy to add a service to the remote access check exemption list. And once the service is there, your non-admin folks will be able to control the service as desired.
To add your service to the list, step by step:
Start the Windows Registry Editor (“Regedit”) on the remote computer. Since it’s an admin tool, you’ll need to be an administrator to run Regedit:
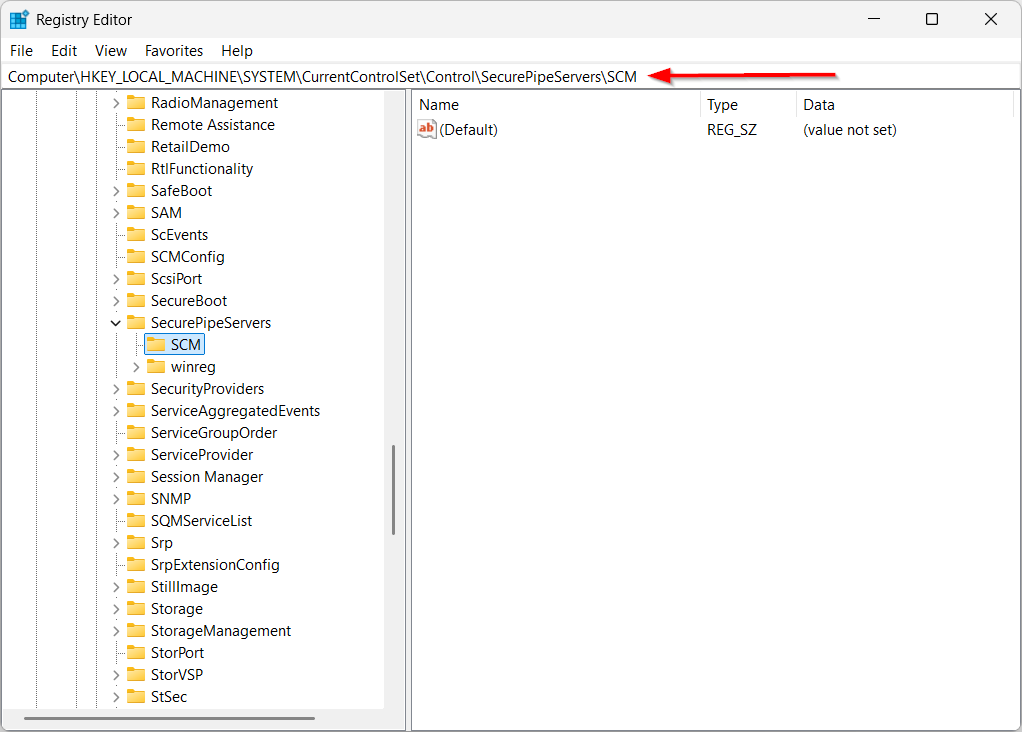
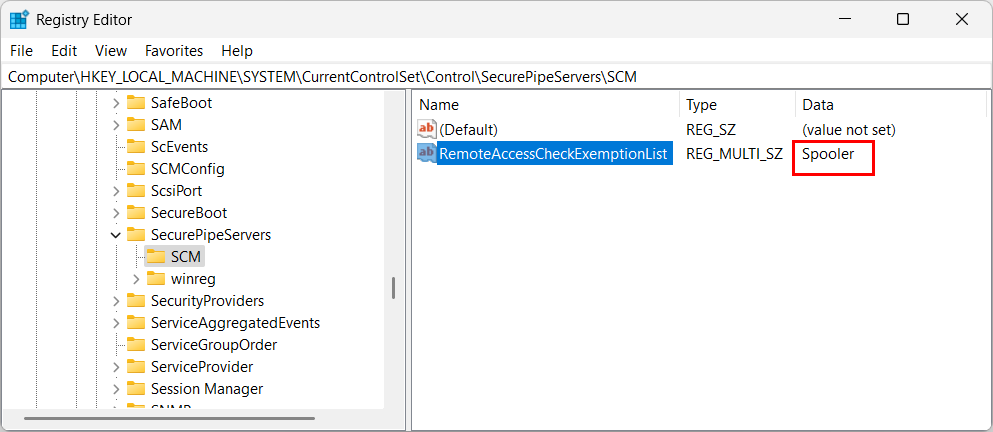
Navigate to this key:
Computer\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurePipeServers\SCM
If you don’t see a SCM key — which is normal on some systems — create it by right-clicking the SecurePipeServers key on the left and selecting
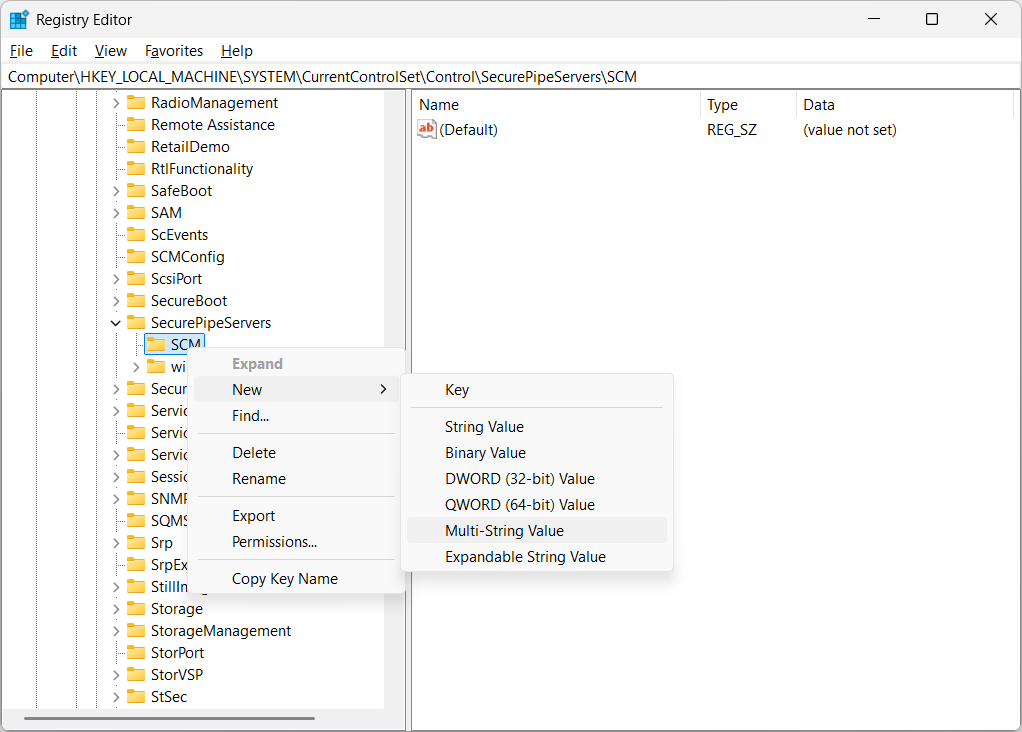
New > Key .In the left panel, right-click the SCM key and select
New > Multi-String Value :In the new value that gets created on the right, set the name to RemoteAccessCheckExemptionList:
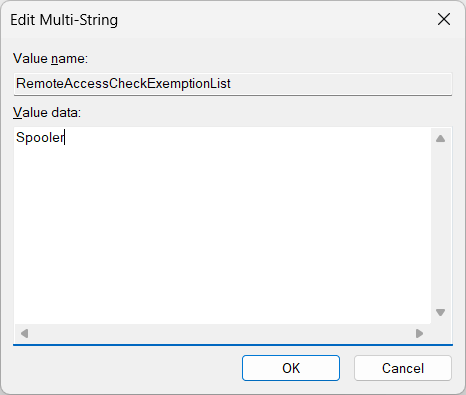
Double-click RemoteAccessCheckExemptionList to edit its value. In the window that comes up, add the name of your service. But be sure to use your service’s “real” name and not its display name, which may be different.
For example, here’s what that looks like when we added Print Spooler, where the service name is Spooler:
Feel free to add multiple services if you like. Just hit the return key, enter another name and keep going.
Click OK once you’re done.
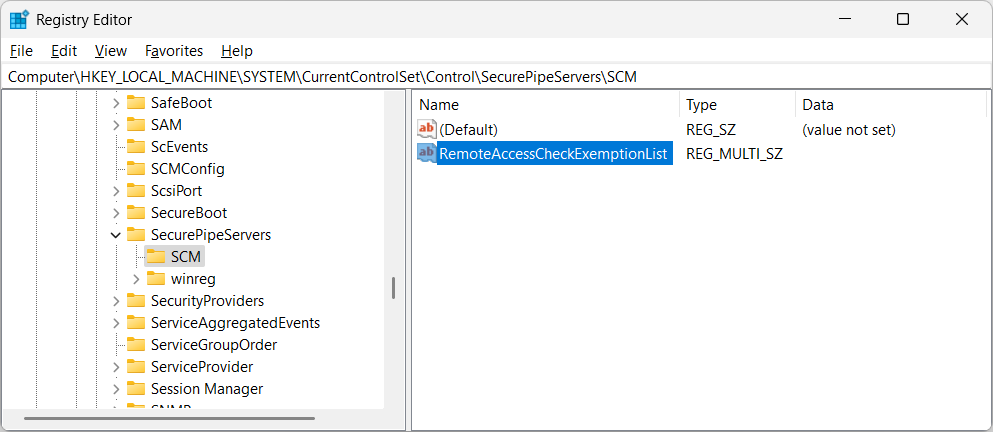
Back in the main Registry Editor window, you should now see your service(s) in the RemoteAccessCheckExemptionList value:
Finally, close Registry Editor.
And with your service on the remote access check exemption list, your non-admin users with rights to the service shouldn’t have any trouble manipulating the service. The dreaded “access denied” error will be a relic of the past.
Coming soon: Service Security Editor will update the remote access check exemption list for you
Our team has already started sketching how to enable non-admin remote access with Service Security Editor. And once that new version of our free software is out, you won’t have to read technical articles from Microsoft or mess with the Windows Registry — unless you really, really want to. 🙂