
Like you, the majority of our work day is spent in front of a computer.
Indeed, most of the time you will find us wrestling with popular Windows applications — like Microsoft Word, Google Chrome and Acrobat Reader. But there are a few lesser-known programs that we have grown to depend on as well.
Here are three of the best free tools we use all the time — and can heartily recommend:
1. FileMenu Tools: Turbocharge your right-click menu with common file operations
Many of our daily tasks revolve around files. We’re constantly opening documents, copying images and composing command lines that require file paths.
For those operations, Lopesoft’s FileMenu Tools has been a godsend.
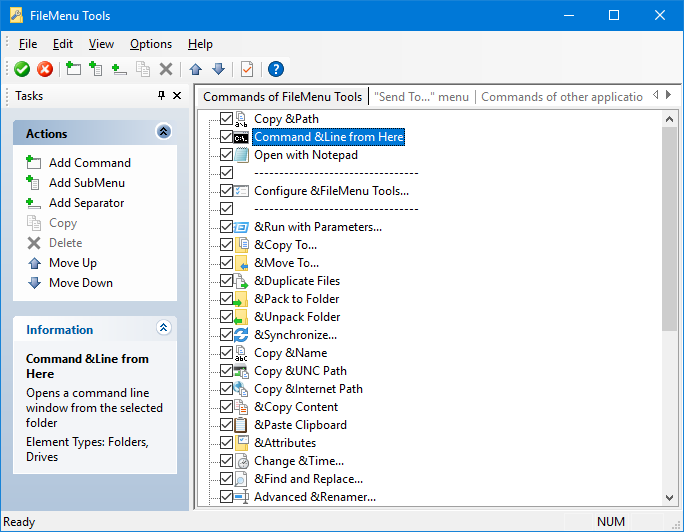
This Windows Explorer extension includes over 35 file operations that you can add to Explorer’s right-click menu:
Our favorites include:
Copy Path: Copies the full path to the selected file(s) into the Windows clipboard. Saves time when we have to open the file in another application or add it to a command line. Just paste and go!
Command Line From Here: Launches the command prompt window, already set to the current folder. Much faster than running CMD and CD’ing.
Open with Notepad: Automatically send a file to Notepad, instead of having to start Notepad, click File > Open and browse to the file.
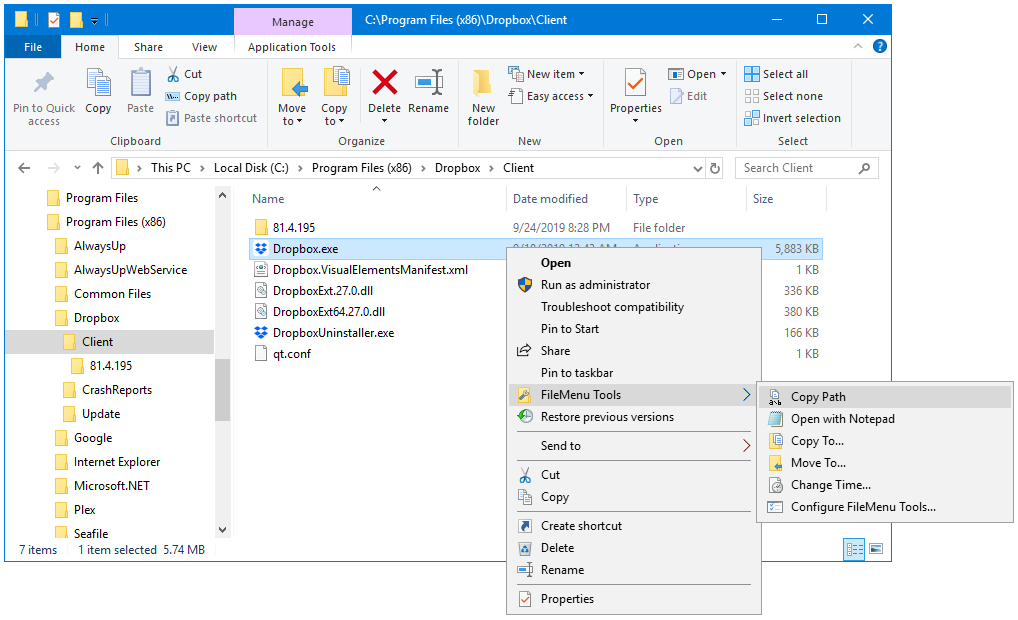
FileMenu Tools is integrated with Windows File Explorer and is very easy to use. Here you can see us copying the full path of the Dropbox executable (C:\Program Files (x86)\Dropbox\Client\Dropbox.exe) to the Windows clipboard — with just a couple of clicks:
We use the free version of FileMenu Tools but you can purchase the full package to unlock advanced features.
2. AbstractSpoon ToDoList: Increase productivity by tracking & organizing important tasks
For our day-to-day planning — and to make sure that we don’t forget our brilliant but ambitious ideas — we turn to AbstractSpoon’s ToDoList.
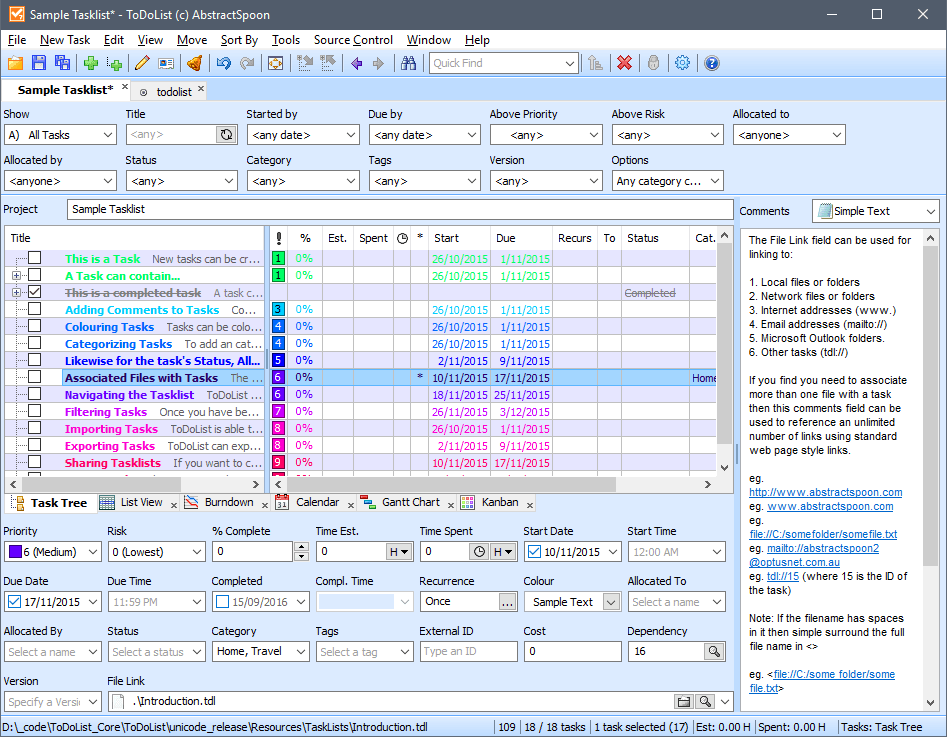
This attractive Windows application uses a time-tested tree structure to organize your body of work. You start with one or more top level goals and break them down into actionable steps.
Each step/task can have over 20 properties that provide relevant context, including “priority”, “due date”, “percent complete” and “cost”.
ToDoList helps us keep track of:
Topics for upcoming blog articles
What to put in each new release (and when to make it available)
Standard email templates, that we can copy & paste into Gmail
Useful but difficult-to-remember commands for managing our UNIX servers
And much more!
And to top it off, ToDoList is actively maintained by a passionate and engaged developer. You will not be disappointed by his responsiveness and attention to detail.
3. Pure Text: Easily paste simple text from the clipboard
I really hate it when I copy text from one application, paste it into another and it comes over with all its formatting. Most times I just want the simple text — with zero decoration.
To get my desired result, I would perform the following dance:
Start Notepad
Paste into Notepad (to produce plain text)
Select all the text
Copy the text
Paste the plain text into my target application
Easy to do but definitely a waste of time.
Enter PureText, a ridiculously simple program that strips all formatting from the clipboard so that we can paste plain text in a single keystroke. What a lifesaver!
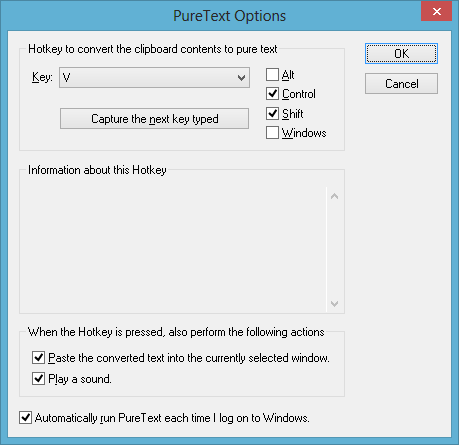
PureText runs as an icon in the task tray area. You assign it a “hotkey” and whenever that key is pressed, it will paste plain text. Here you can see that we have assigned Ctrl-Shift-V (which is close to Ctrl-V, the key combination that performs a “regular” paste):
Once you have installed PureText, it will be difficult to use a computer without it. It’s one of the first apps we install on a new PC.
So those are three Windows utilities that make a difference in our day-to-day. Download, install and enjoy!
What free applications do you recommend?
We would love to hear your advice and opinions! Please let us know in the comments section.





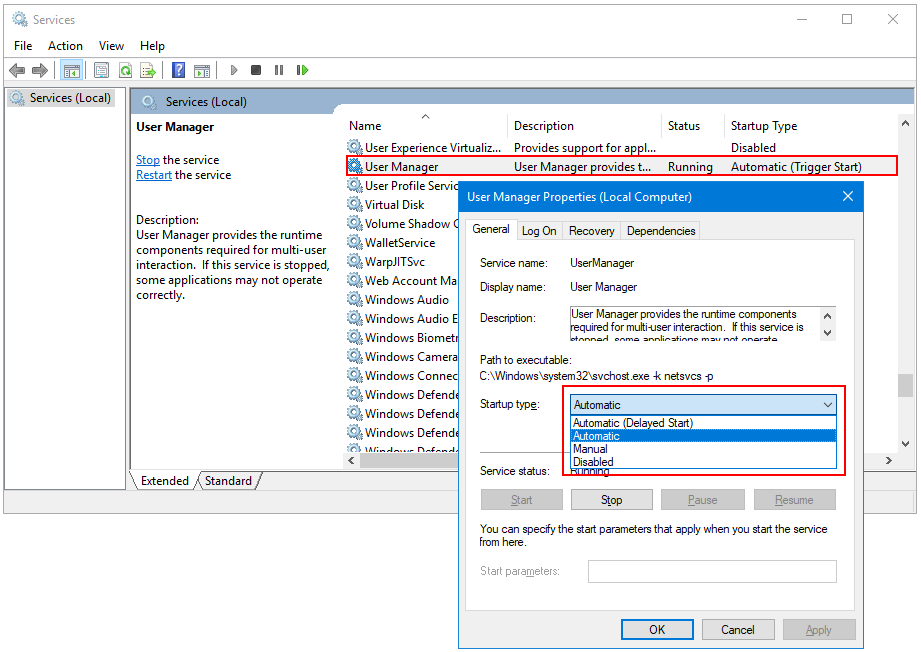




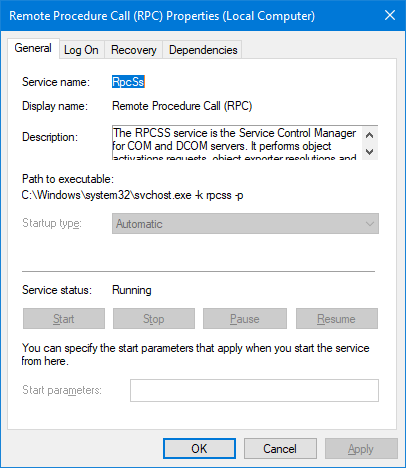
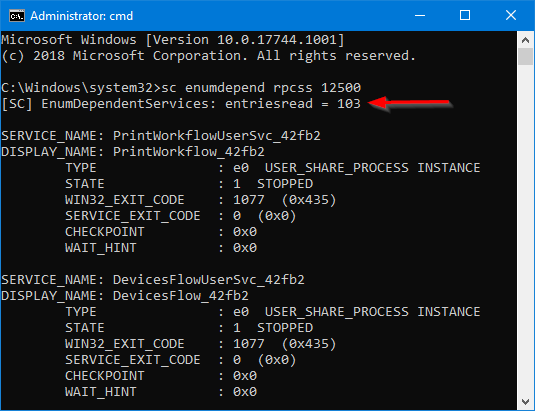
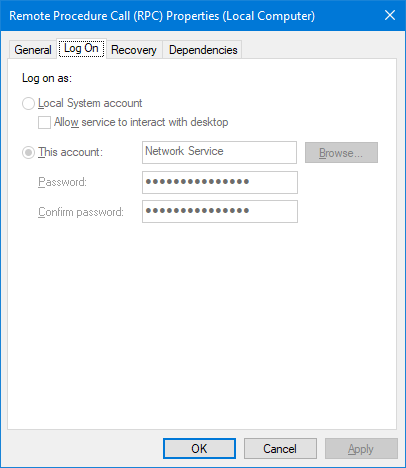



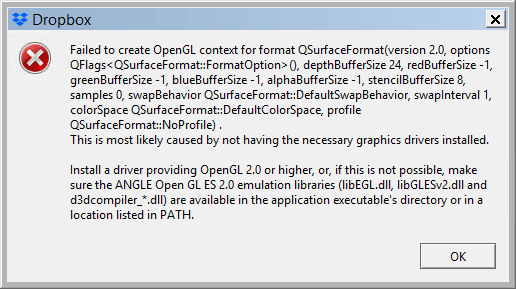
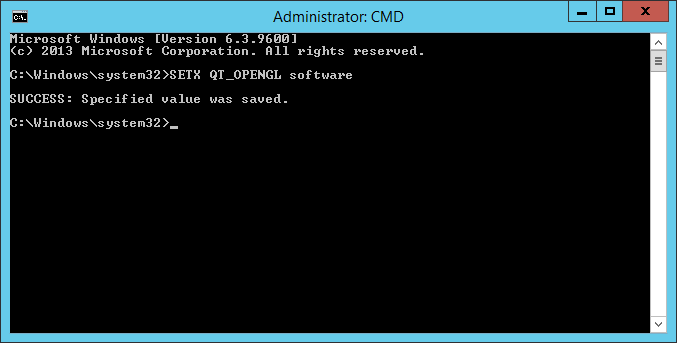
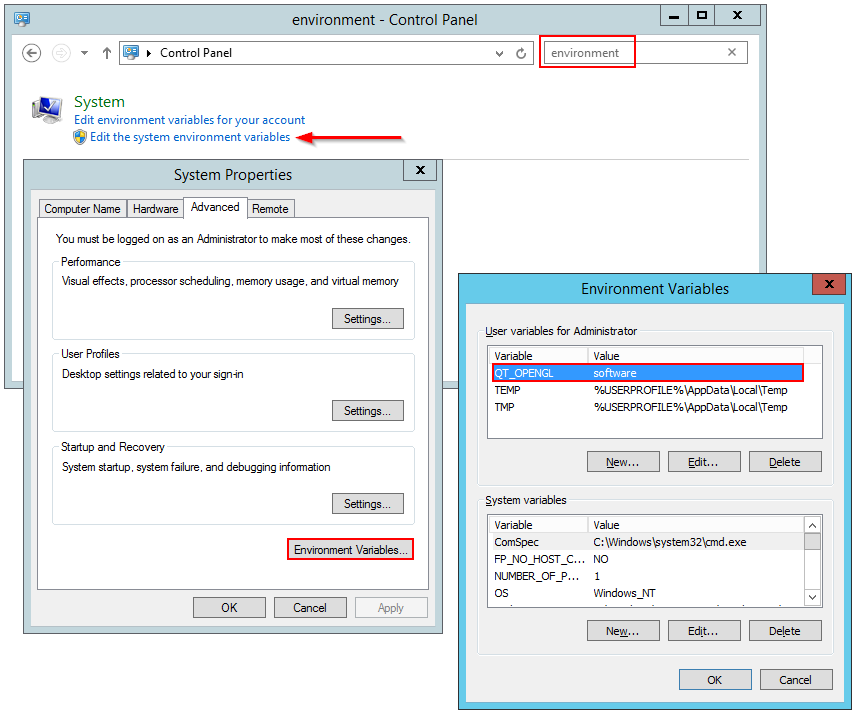




 I found a way to work around this issue, at least in my environment,
I found a way to work around this issue, at least in my environment,
![OneDrive Version 23.48: Trouble Running in Session 0 [RESOLVED]](https://www.coretechnologies.com/blog/wp-content/uploads/onedrive-error-150x150-1.webp)
