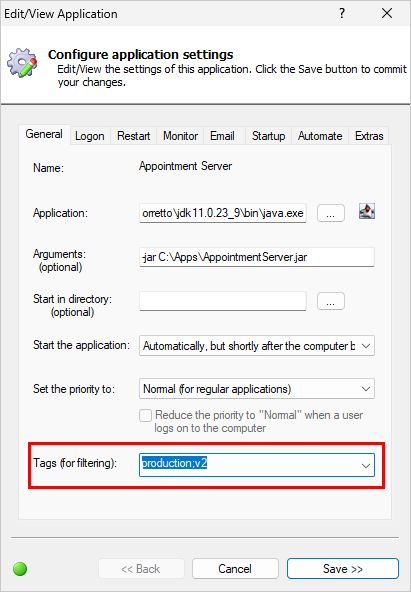
In this article…
What is the Windows Time (W32Time) service?
The Windows Time service (W32Time) implements the Network Time Protocol (NTP) specification to synchronize the date and time of computers managed by Active Directory (AD).
It may not be obvious but keeping the clock accurate and synchronized with the rest of the domain is an essential task. That’s because modern authentication methods (like Kerberos V5) may fail when networked machines are not coordinated. As such, W32Time plays a key role on computers joined to Active Directory. Otherwise, it’s not really important.
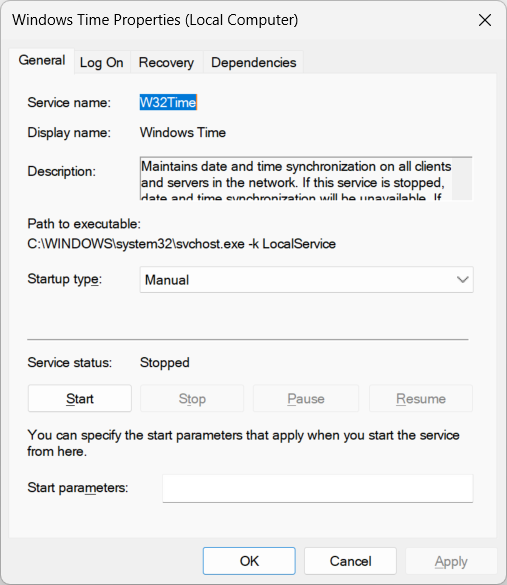
The Windows Time service runs as LocalSystem inside the service host process, svchost.exe:
And because the service doesn’t need to run all the time on most systems, it’s often classified as Manual (Trigger start). In that case, it only wakes up to run if:
a program or another service asks it to start, or
whenever a one or more Windows “trigger” events occur.
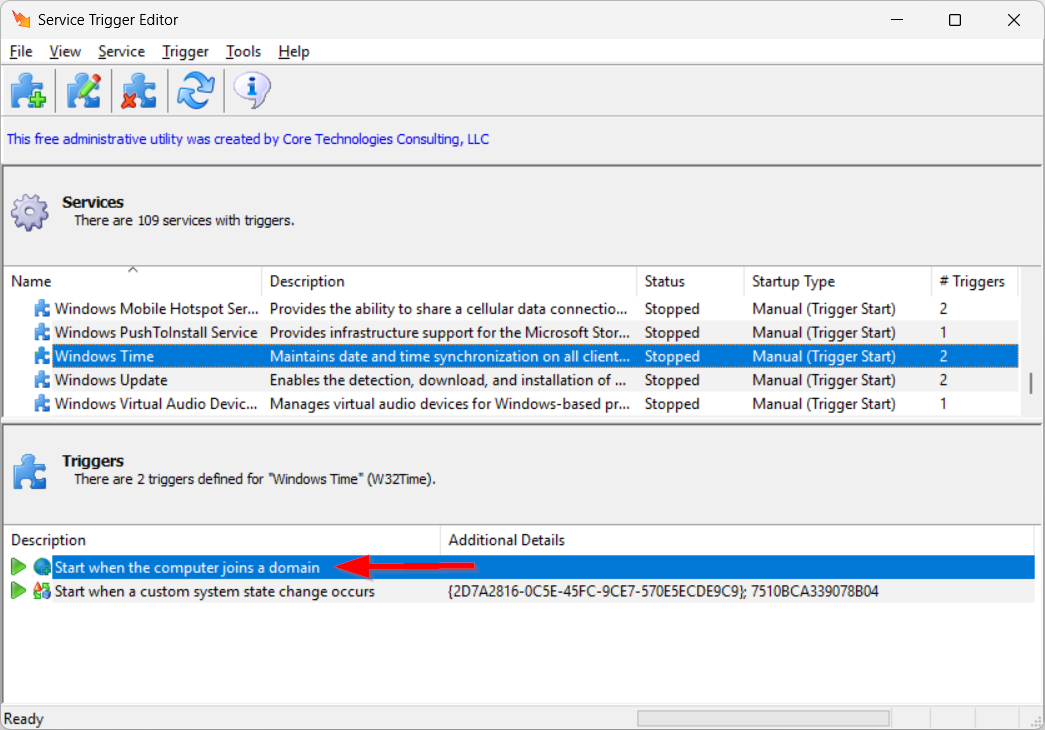
Indeed, if you examine the trigger events with our free Service Trigger Editor utility, you will see that Windows will launch the service whenever “the computer joins a domain”:
That makes sense. When your PC joins a network, Windows Time jumps into action and synchronizes your clock if you’re connected to Active Directory. Afterwards, it stops and waits for the next network-join event or request to start. It’s a much more efficient way to operate versus starting at boot and running 24/7.
What happens if I stop W32Time?
If you’re working in a home environment or without Active Directory, not much will happen if you stop the Windows Time service. In fact, most of the time you will find that the service is idle on your computer.
And even if you’re in a corporate environment with networked PC’s, temporarily stopping W32Time should be fine. If it’s needed by a program or another service, they will simply start W32Time.
Is it OK to disable the Windows Time service?
It’s fine to disable the Windows Time service if your computer isn’t joined to Active Directory. But don’t expect a huge, CPU-saving impact because the service doesn’t spend much time running in that situation anyway.
However, if your computer is joined to Active Directory, you should keep the service active. You don’t want to have any trouble signing in to your PC!
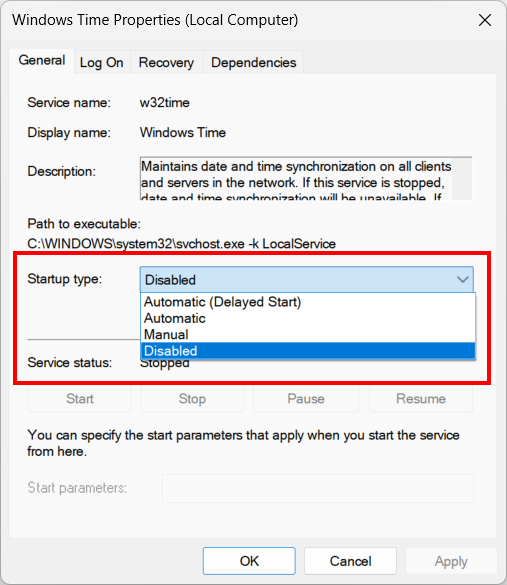
In any case, if you insist on disabling the service you can do so the conventional way — by setting the Startup type to Disabled in the Services app:
After you make that change, no person or program will be able to start W32Time. It will be inert.
But if that’s not good enough and you really want to get rid of the service, you should run W32tm /unregister from an elevated command prompt. That command will stop the service (if necessary) and uninstall it from the list of services. Afterwards, Windows Time will be completely gone from your system.
Don’t worry; if you change your mind and the Windows Time service becomes your friend again, simply run W32tm /register to restore the service. You’ll be good to go.
Questions? Problems?
If you would like to know more about the Windows Time service, or you have a specific problem, please feel free to get in touch. We’ll do our best to help you!